How to hide connections between your crypto and you, your pseudonames, or your other crypto
First of all, keep in mind:
- the less money, the less attention;
- whoever can trade in information is probably trading in information;
- always use the Tor network.
Monero
Obfuscation is secure: yes, very much so
Obfuscation is stealthy: yes
Suspicious to use: a little
The best, near-perfect solution. The Monero cryptocurrency was designed with this in mind. All you have to do is download the wallet app and read the simple guide. It is easy to get Monero (XMR) on exchangers. Next, you need to create a new XMR address in your wallet and send XMR to it using the obfuscation option. Unlike bitcoin, the transaction does not appear on the blockchain. Your XMRs will appear “out of nowhere” at the new address. Information about the origin of these XMRs is only available to you and only until you delete it from your computer. After that, you can transfer the XMRs to another new address without obfuscation and with a record in the blockchain to look a little less suspicious for the next recipient. Finally, XMRs are exchanged for anything.
It is worth noting that law enforcement and financial organisations understand that XMRs should be treated with suspicion. Therefore, it is better to exchange them for bitcoins / USDT / or whatever before linking the cryptocurrency to your identity.
It’s a bit more complicated in practice, but worth it. The cryptography behind Monero is beyond the reach of even governments. And you don’t have to trust anyone – there’s only your secure operating system (Tails, Whonix, etc.), the Tor network and the Monero wallet.
You might also want to check out other privacy coins such as Zcash.
Bitcoin mixers (tumblers)
Obfuscation is reliable: yes, but it depends on the service and they are extremely difficult to audit
Obfuscation is stealthy: no
Suspicious to use: very much so
In theory, the best possible outcome: their cryptography and algorithms are robust and your transaction cannot be traced. And you get bitcoins that smell really bad. Only bitcoins withdrawn from a TOR drug marketplace are worse.
“Obfuscation is reliable” shouldn’t be taken at face value. Bitcoin mixers do not publish their source code, the quality of their obfuscation cannot be verified. Mixers have often been caught cheating users by not even trying to mix bitcoins. Not to mention mixers with insufficiently secure mixing mechanisms: weak cryptography can even be found in military and first responder radios that have been in use for decades, because the manufacturer hasn’t opened its code to public scrutiny [1, 2]. Mixers can also see exactly which addresses users are using to withdraw their mixed BTCs. And it is unknown who owns them and what they do with transaction logs (despite the ubiquitous “we never keep logs!”): such logs are worth a lot of money on the information market.
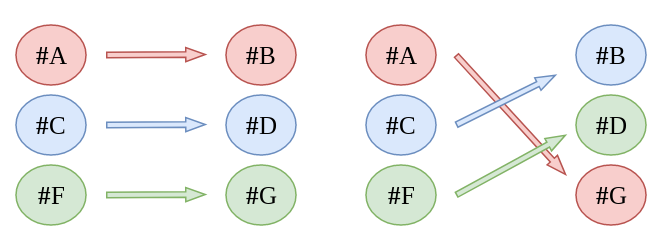
The basic principle of mixing is easy to explain. Let’s say three different users want to transfer cryptocurrency from one address to another. If this is done through a mixer, the user doesn’t get his cryptocurrency, he gets someone else’s cryptocurrency. And someone else gets their cryptocurrency. This throws the trackers off the scent.
Let’s say user #1 transfers 0.1 BTC from address #A to address #B, user #2 transfers 0.1 BTC from #C to #D, and user #3 transfers 0.1 BTC from #F to #G. You can see this relationship in the blockchain, as shown by the colours in the figure below. Mixing is what happens on the right in the image below: the link in the blockchain leads to the wrong user.
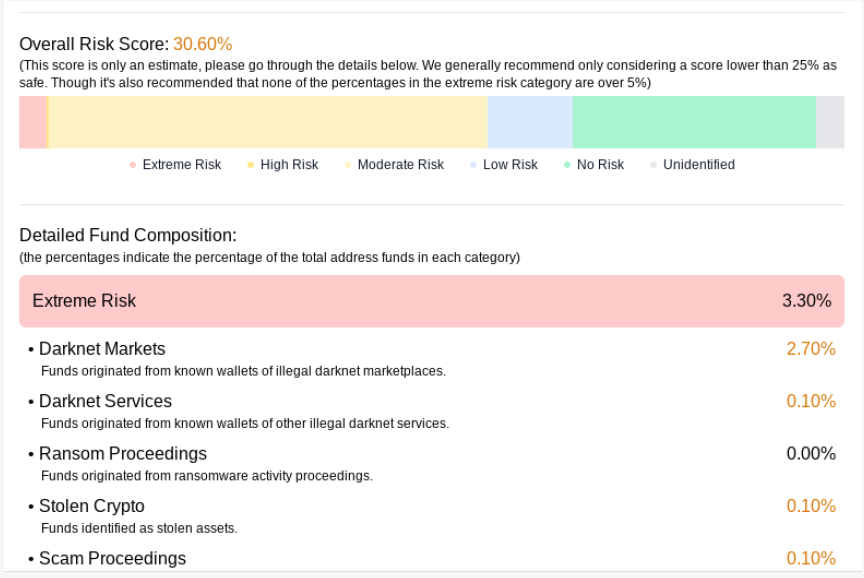
But the vast majority of exchanges (e.g. those listed on BestChange.com) and platforms (e.g. Binance, Kraken) will at best not take such bitcoins from you and send them back to you. Very often, they will keep the bitcoins until you provide them with an ID and an explanation that the funds are not of illegal origin. They verify the origin of the bitcoins by ordering cryptocurrency AML checks from analytics companies.
These companies know which cryptocurrency addresses belong to which actors: cryptocurrency exchanges, traders, darknet sites, miners. And their clients receive reports on the addresses or transactions they are interested in:
Such bitcoins are suitable for payment of “black” services and are accepted by the few exchanges that are not interested in KYC and AML. If this suits you, there is the question of the trustworthiness of the mixers. On the bitcointalk.org forum (founded by Satoshi Nakamoto), mixer owners used to start forum threads where forum users would report if they were satisfied with the service. As of 2024, all mentions of mixers have been scrubbed from the forum. But you can read the forum pages that were saved before mixers were banned using a service like Wayback Machine. And look for reviews elsewhere.
CoinJoin
Obfuscation is reliable: yes, sort of, unless your life depends on it
Obfuscation is stealthy: no
Usage is suspicious: yes, but less so than BTC mixers
CoinJoin is also a way to mix bitcoins. Unlike bitcoin mixers, you don’t have to trust a service: bitcoins cannot be stolen (non-custodial service, doesn’t hold your assets in custody), and the reliability of CoinJoin services is judged by the open source code and data.
CoinJoin does offer privacy, but it’s not considered strong by some, and they call it privacy by deniability. Don’t use CoinJoin to hide something really important.
Do your own research to choose a particular CoinJoin service. There aren’t many of them.
Bitcoins from CoinJoin are considered less dirty than those from BTC mixers. Here’s a quote from Trezor:
… coins that could be deemed high-risk are refused from joining the coinjoin. That said, some exchanges may ask further questions when they encounter coins coming from a coinjoin, so we recommend learning about individual exchange policy before depositing coinjoined funds.
Learning about the concept of lightning channels in the bitcoin protocol can help with the “Usage is suspicious” clause.
This article has
- a good description of CoinJoin;
- links to some CoinJoin services;
- links to detailed descriptions of its functionality;
- and other bitcoin-related mixing methods (mostly theoretical).
Tornado Cash
Obfuscation is reliable: looks like it is
Obfuscation is stealthy: no
Usage is suspicious: yes, very much so, and even illegal in USA
This is a mixing protocol for the Ethereum blockchain.
The cool thing is that it can’t be shut down, even if you ban and sanction it (as the US has done). This software code has a life of its own, and any user can set up their wallet for mixing via Tornado Cash in a matter of minutes.
It seems that the quality of the mix is quite reliable, as is the protocol itself and its front-end. If you are interested, you can check out these security audits: Tornado Cash Smart Contracts Audit and Frontend Security Audit.
Because it’s a mixer, and it’s under US sanctions and its creators are in jail, coins from Tornado Cash are blocked by some services that provide functionality for wallets like MetaMask. You should read advice on that by Tornado Cash community:
After the OFAC sanctions most RPC endpoints have censored deposits, make sure your wallet is manually configured to a working endpoint. See options on chainlist.org and how to how to configure MetaMask.
Exchanges
If you exchange one cryptocurrency for another at exchange #1, then for something else at exchange #2, then again through the Telegram exchange (using Tor, of course), a potential attacker would have to get exchange data from all three exchanges. If you’re doing something serious, using only such schemes won’t help you sleep at night. But if the scheme is well thought out and complicated, it can serve you well.
You need to have an understanding of the capabilities of a potential adversary and their will to spend resources on you.
And be aware of your lack of understanding. Is it okay to use exchanges that are known only in your language and/or geographical region? If you withdraw cash through an exchange, will analysts know that you have been to one of their available geolocations? What about crypto ATMs? CCTVs? Small Telegram exchangers from a small country overseas?
You also need to be aware that information about exchanges is valuable. Some exchangers sell it, some illegaly provide it to law enforcement or organised crime.
So?
It is often necessary to combine the above methods to achieve successful and undetectable obfuscation. Play it safe.

There are no comments here yet. Be the first one!